For 2010, Microsoft cleaned over 20 million computers of malware(s) in the United States alone. Ladies and gentlemen, this has got to stop. It is time to squash this passive attitude about your computer, it is time for a grand catharsis!
For those that do not have a genuine copy of Windows, tsk-tsk, shame on you. The one thing that you should not be cheap with is your OS (Operating System).
For those PC users that have a genuine copy of Microsoft Windows please download Microsoft’s Security Essentials and install it on your machine. MSE is lightweight and intelligent, to say the least. I’ve tried Norton, Kaspersky, AVG and McAfee, and they all gave me headaches and used too many system resources. MSE was a breath of fresh air and I haven’t looked back.
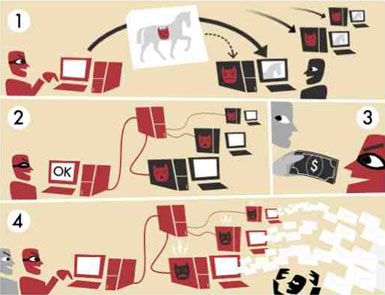
Now, why am I plugging this software? Because some of you are unknowingly running a bot (virus, trojan, etc.) on your computer. The number of infected machines change from quarter to quarter, but in 2007 it was estimated by the BBC that one-fourth of all machines on the Net were infected. The above picture breaks down how a botnet is used to send spam (illustration comes courtesy of Tom-B of Wikipedia).
To explain the illustration, it works like this:
- The red guy with the bandit mask is a botnet operator. A botnet operator infects a user’s computer with a virus or worm (often multiple). The goal is to store a malicious program (dubbed ‘malware’) inside the user’s computer. This bot, or malware, is usually stored unbeknownst to the user. It masquerades as a useful program – much like the Trojan horse carried inside the gates of Troy contained Greeks waiting to siege the city.
-
Once the bot is installed in a user’s computer, it can independently log into an Internet Relay Chat (IRC) server or web server and do the bidding of the botnet operator.
-
Spammers can then buy the information these bots relay or pay the operator to program the spam messages they wish to send.
-
The infected computers are programmed to send out spam messages, the user’s reputation is damaged, and his entire system is compromised.
For those who truly understand the intricate devilry of botnet operators and spammers, it is difficult not to feel violated, distraught, or just plain angry. In part 3 of this series we’ll examine the history of spam, bots, and the future of malware. We can only hope malware doesn’t have a future, but that is up to you to deny it one. Stay tuned.